The Web Application Firewall (WAF) protects your web applications from common web exploits by filtering and monitoring HTTP traffic between a web application and the Internet. You can protect your resources based on specified conditions. For AWS Customers – the AWS WAF is one of the best choices as it gives users many advantages over other 3rd party WAF services. AWS WAF lets you monitor HTTP(S) requests that are forwarded to an Amazon CloudFront distribution, an Amazon API Gateway REST API, an Application Load Balancer, or an AWS AppSync GraphQL API. AWS WAF also lets you control access to your content based on conditions that you specify, such as the IP addresses that requests originate from or the values of query strings. Under AWS, it is easy to set up and to select pre-configured WAF-Rules that allow you to deploy a decent WAF for your application within minutes. Most of AWS users rely on Amazon’s experts to cover the basics (and beyond). A recently published article by Osama Elnaggar, revealed a fairly basic weakness that relies on AWS-WAF, which the average user might oversee. Deep within the AWS WAF documentation, Amazon notes that its default WAF behavior is to forward only the first 8KB of the request body to AWS WAF for inspection. The inherent weakness that lies here is that any malicious payload that starts after the 8KB limit in a POST request will completely bypass your WAF. Unfortunately, by default Amazon doesn’t block POST requests larger than 8KB in size. AWS default body size restriction is set to 10KB – so an attacker can easily bypass this restriction by padding their payload and exploiting the WAF’s blind spot, the 8KB – 10KB range.
Test if your AWS WAF is vulnerable
There is more than one way to verify if your AWS WAF setup is vulnerable or not. One option is to pad a POST request you know your WAF blocks and see if it succeeds or not. Another option is to go through your Web ACL, looking for any rule that limits uploads to 8K. To do so, you can:
- Login to your AWS Console and navigate to the WAF & Shield service
- Select the WEB ACLs tab and in the upper right corner, click the “Download web ACL as JSON”
- Save the downloaded file.
- Open the JSON file in a text editor and search for SizeConstraintStatement string.
- If you find it – verify that it is applied to the BODY and that it detects a payload greater than 8192 it is set to Block (As shown in this JSON example)
- If so – you are at risk.
- If you didn’t find it, your web app is at the mercy of the default setting.
Mitigation
An important note before taking any action – is to avoid failing your production environment. This could be reached by setting the new/updated rule to “Count” mode. This will allow you to detect any application pages that use payloads that are > 8KB (for example, any page that supports file uploads). Detected pages will have to be whitelisted. To mitigate this attack, simply add a Size Constraint rule to block requests with a BODY greater than 8192 (8KB) in size. This can be done via one of these methods:
- Copy and paste the attached JSON example in the section above as a new rule.
- Go to Web ACLs → Add rules → Add my own rules and rule groups configure the rule as shown in the images below.
- Click Add Rule.
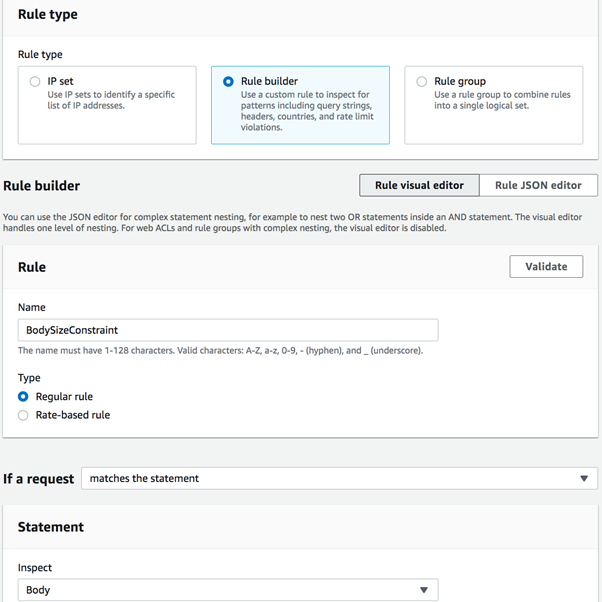
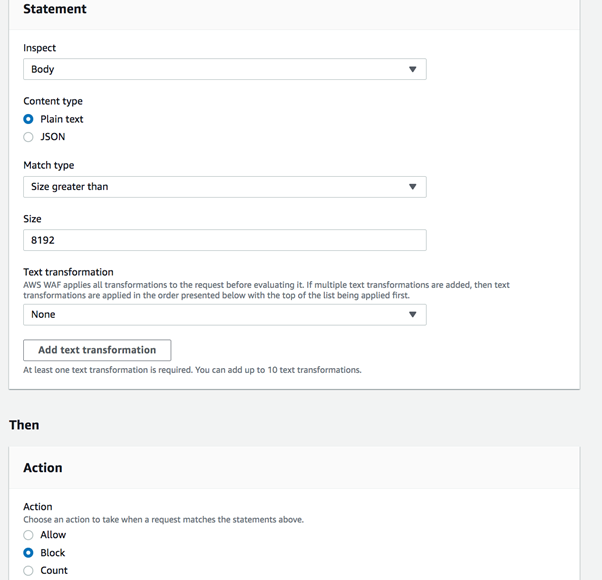
It is recommended that you set this rule with high priority to allow it to run before your other rules. Finally, retest the attack and verify that these requests are being blocked.
Based on an article written by Osama Elnaggar.
לסרטוני הדגמה בעברית של החולשה לחצו כאן





